- Welcome to Cobra Forum.
Recent posts
#81
Webserver / On WordPress website hosted on...
Last post by Suhitha - Sep 26, 2025, 05:08 AMQuestion: On WordPress website hosted on Plesk for Linux server, pagination buttons in WordPress Admin dashboard do not work as expected
Symptoms
Cause
nginx processing the variable HTTP_HOST differently when serving HTTP/3 requests:
https://trac.nginx.org/nginx/ticket/2281
Resolution
1.Connect to the server via SSH.
2.Create or edit file /etc/nginx/fastcgi.conf and add the following configuration to it:
3.Restart nginx to apply the changes:
Symptoms
- On a WordPress website hosted on a Plesk for Linux server, pagination buttons in WordPress Admin dashboard do not work as expected.
- HTTP/3 is enabled.
- PHP handler on the domain is set as FPM application served by nginx in the menu Domains > example.com > PHP.
- When WordPress debug mode enabled, the following PHP warning appears on the website:
Code Select
PHP Warning: Undefined array key "HTTP_HOST" in /var/www/vhosts/example.com/httpdocs/wp/wp-admin/includes/misc.php
Cause
nginx processing the variable HTTP_HOST differently when serving HTTP/3 requests:
https://trac.nginx.org/nginx/ticket/2281
Resolution
1.Connect to the server via SSH.
2.Create or edit file /etc/nginx/fastcgi.conf and add the following configuration to it:
Code Select
fastcgi_param HTTP_HOST $host;3.Restart nginx to apply the changes:
Code Select
# service nginx restart #82
Webserver / How to enable Step Debugger on...
Last post by Suhitha - Sep 26, 2025, 04:58 AMQuestion: How to enable Step Debugger on PHP on a Plesk server?
Applicable to:
Question
How to enable XDebug's Step Debugger on PHP on a Plesk server?
Answer
Warning: The following set of instructions include the restart of a service. Consider restarting during maintenance hours to minimize downtime.
1.Log into Plesk
2.Ensure that XDebug as an extension is enabled at Tools & Settings > PHP Settings > PHP version (e.g. 8.3).
3.Add the XDebug configuration to the 50-xdebug.ini file. It's located at /opt/plesk/php/<php_version>/etc/php.d/50-xdebug.ini. Common configuration include:
4.Restart PHP service:
Note: Change the number in case it's a different PHP version.
Applicable to:
- Plesk for Linux
Question
How to enable XDebug's Step Debugger on PHP on a Plesk server?
Answer
Warning: The following set of instructions include the restart of a service. Consider restarting during maintenance hours to minimize downtime.
1.Log into Plesk
2.Ensure that XDebug as an extension is enabled at Tools & Settings > PHP Settings > PHP version (e.g. 8.3).
3.Add the XDebug configuration to the 50-xdebug.ini file. It's located at /opt/plesk/php/<php_version>/etc/php.d/50-xdebug.ini. Common configuration include:
Code Select
; Enable xdebug extension module
zend_extension=xdebug.so
xdebug.mode=debug,develop
xdebug.client_host=127.0.0.1
xdebug.client_port="9003"4.Restart PHP service:
Code Select
# systemctl restart plesk-php83-fpmNote: Change the number in case it's a different PHP version.
#83
Webserver / How to update ImageMagick to v...
Last post by Suhitha - Sep 26, 2025, 04:48 AMQuestion
How to update ImageMagick to version 7 in CentOS 7.9 in PHP 8.2?
Answer
Warning: This scenario was not tested with Plesk, thus not supported. To run it, you will have to remove the ImageMagick 6, that allows ImageMagick to run in php7 and php8 in 6.9. All the actions should be performed at own risk.
1.Connect to the Plesk server via SSH.
2.Remove the current version of ImageMagick:
Code Select
# yum remove ImageMagick ImageMagick-devel3.Download remi repository:
Code Select
# yum install epel-release yum-utils -y http://rpms.famillecollet.com/enterprise/remi-release-7.rpm4.Enable it:
Code Select
# yum-config-manager --enable remi5.Install ImageMagick from remi repository:
Code Select
# yum install ImageMagick7 ImageMagick7-libs ImageMagick7-devel -y6.Install the development tools to compile the module:
Code Select
# yum groupinstall 'Development Tools'7.Install the develpment package for plesk-php82:
#yum install plesk-php82-devel
8.Install imagick extension for Plesk PHP 8.2:
Code Select
# /opt/plesk/php/8.2/bin/pecl install Imagick9.When the process is finished, rename .so file, so that it is not replaced during updates:
Code Select
# mv /opt/plesk/php/8.2/lib64/php/modules/imagick.so /opt/plesk/php/8.2/lib64/php/modules/imagick_new.so
10.Execute the following command to add the extension:
Code Select
# echo "extension=imagick_new.so" > /opt/plesk/php/8.2/etc/php.d/imagick.ini #84
Webserver / Unable to connect to MSSQL usi...
Last post by Suhitha - Sep 26, 2025, 04:26 AMQuestion: Unable to connect to MSSQL using web.config: Cannot open database "ASPState" requested by the login. The login failed.
Applicable to:
Symptoms
Server Error in '/' Application.
Cannot open database "ASPState" requested by the login. The login failed.
Login failed for user 'dbuser'.
Description: An unhandled exception occurred during the execution of the current web request. Please review the stack trace for more information about the error and where it originated in the code.
Exception Details: System Data.SqlClient.SqlException: Cannot open database "ASPState" requested by the login. The login failed.
Login failed for user 'dbuser'.
Source Error:
An unhandled exception was generated during the execution of the current web request. Information regarding the origin and location of the exception can be identified using the exception stack trace below.
Stack Trace:
[SqlException (0x80131904): Cannot open database "ASPState" requested by the login. The login failed.
Login failed for user 'dbuser'.]
Cause
Session State misconfiguration on IIS
Resolution
1.Connect to the Plesk server via RDP.
2.On the IIS Manager, go to Sites > domain.com > Session State
3.On the Session State screen, under the Session State Mode Settings, I selected 'In process' (see the arrow):
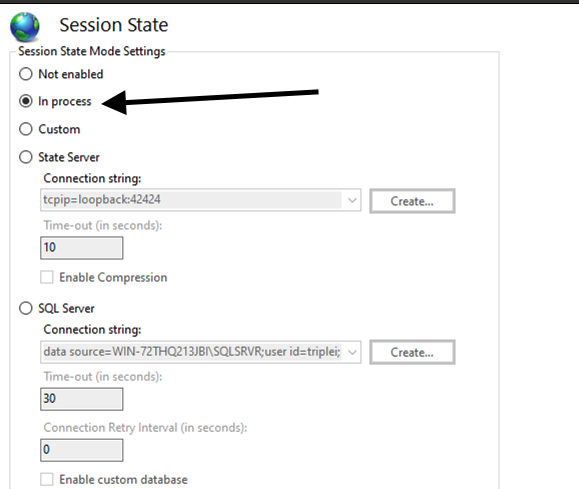
4.On the right, under the Actions pane, click Apply.
5.Open a command prompt as Administrator and run the following command:
Applicable to:
- Plesk for Windows
Symptoms
- Configuring a connection to MSSQL in web.config produces the following error:
Server Error in '/' Application.
Cannot open database "ASPState" requested by the login. The login failed.
Login failed for user 'dbuser'.
Description: An unhandled exception occurred during the execution of the current web request. Please review the stack trace for more information about the error and where it originated in the code.
Exception Details: System Data.SqlClient.SqlException: Cannot open database "ASPState" requested by the login. The login failed.
Login failed for user 'dbuser'.
Source Error:
An unhandled exception was generated during the execution of the current web request. Information regarding the origin and location of the exception can be identified using the exception stack trace below.
Stack Trace:
[SqlException (0x80131904): Cannot open database "ASPState" requested by the login. The login failed.
Login failed for user 'dbuser'.]
Cause
Session State misconfiguration on IIS
Resolution
1.Connect to the Plesk server via RDP.
2.On the IIS Manager, go to Sites > domain.com > Session State
3.On the Session State screen, under the Session State Mode Settings, I selected 'In process' (see the arrow):

4.On the right, under the Actions pane, click Apply.
5.Open a command prompt as Administrator and run the following command:
Code Select
c:\> iisreset #85
Webserver / How to block user-agents in Pl...
Last post by Suhitha - Sep 26, 2025, 03:49 AMQuestion
How to block user-agents in Plesk Control Panel on Linux?
Answer
To block a specific user agent to reaching the Plesk control panel, use these steps:
Note: the command will cause a brief downtime, while the frontend is being restarted:
Make a non-redirect following query with a specified user agent. Now it will return 403:
How to block user-agents in Plesk Control Panel on Linux?
Answer
To block a specific user agent to reaching the Plesk control panel, use these steps:
- Edit the file /etc/sw-cp-server/conf.d/plesk.conf.
- Add the following configuration (where hello, world and helloworld are case-insensitive:
Code Select
map $http_user_agent $badagent {
default 0;
~*hello 1;
~*world 1;
~*helloworld 1;
}- Now paste the if condition within the domain's (the "server" block, where sw-cp-server is listening) configuration file, e.g.:
Code Select
if ($badagent) {
return 403;
}- You should have your file looking closer to this:
Code Select
map $http_x_requested_with $error_doc_format {
default html;
XMLHttpRequest json;
}
map $http_x_forwarded_proto $original_proto {
default $http_x_forwarded_proto;
"" $scheme;
}
map $http_user_agent $badagent {
default 0;
~*hello 1;
~*world 1;
~*helloworld 1;
}
server {
listen 8443 ssl;
listen 8880;
listen 127.0.0.1:8880 default_server;|
include conf.d/*ipv6_ports.inc;
http2 on;
ssl_certificate /opt/psa/admin/conf/httpsd.pem;
ssl_certificate_key /opt/psa/admin/conf/httpsd.pem;
include conf.d/*plesk.inc;
include conf.d/*wpb.inc;
if ($badagent) {
return 403;
}
}- Restart the Plesk frontend:
Note: the command will cause a brief downtime, while the frontend is being restarted:
Code Select
# systemctl restart sw-cp-serverMake a non-redirect following query with a specified user agent. Now it will return 403:
Code Select
# curl -Ik https://example.com:8443 -A "hello"
HTTP/2 403
server: nginx
date: Mon, 24 Mar 2025 19:29:54 GMT
content-type: text/html
content-length: 146 #86
Webserver / How to block user-agents in Pl...
Last post by Suhitha - Sep 26, 2025, 03:41 AMQuestion
How to block user-agents in Plesk Control Panel on Windows?
Answer
Choose a method that suites you most:
Using Filtering Rules on IIS
To block these agents on IIS use the following steps:
Open the IIS Manager
Navigate to the level that you want to block the request (use the top level to apply it to the entire server)
Click on Request Filtering (in IIS part)
Click on the Filters Tab, then click on Add filtering rule... in the Action panel on the right
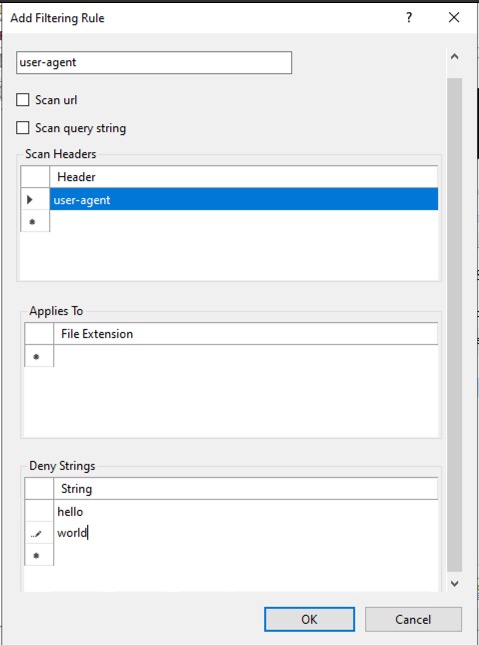
Configure the tab as follows:
Define a name for the rule, in this example is "user-agent"
In the Scan Header field, add the value "user-agent"
In the Deny Strings field, add the values of the user-agents that must be blocked, one per line. In the example, is blocking the user-agents "hello" and "world"
You should add closer to this:
Using URL Rewriting Rules
To create a persistent rule in IIS on URL Rewriting, use the following steps:
1.Open IIS Manager (inetmgr).
2.Select the Server Node (not a specific site).
3.Open URL Rewrite.
4.Click "Add Rules..." on the right.
5.Choose Blank Rule under "Inbound Rules".
6.Click Edit... under "Conditions".
7.Click Add and configure:
8.Click OK.
9.In Action, select "Abort Request".
10.Click Apply and make a non-redirect following query with a specified user agent. Now it will return error aborting the connection:
This solution is persistent across Plesk updates. It affects all IIS-hosted sites, including the Plesk Panel. It does not rely on web.config, which Plesk modifies.
Alternatively, if you prefer to edit the file manually, you can add the following content to file C:\Windows\System32\inetsrv\config\applicationHost.config inside <system.webServer> after line that starts with <proxy enabled="true"...:
CONFIGTEXT: <rewrite>
<rules>
<rule name="Block Bad User-Agents" stopProcessing="true">
<match url=".*" />
<conditions>
<add input="{HTTP_USER_AGENT}" pattern=".*(badbot|malicious-agent|exploit-scanner|hello|world).*" />
</conditions>
<action type="AbortRequest" />
</rule>
</rules>
</rewrite>
It will provide the same effect as the solution proposed above.
How to block user-agents in Plesk Control Panel on Windows?
Answer
Choose a method that suites you most:
Using Filtering Rules on IIS
To block these agents on IIS use the following steps:
Open the IIS Manager
Navigate to the level that you want to block the request (use the top level to apply it to the entire server)
Click on Request Filtering (in IIS part)
Click on the Filters Tab, then click on Add filtering rule... in the Action panel on the right
Configure the tab as follows:
Define a name for the rule, in this example is "user-agent"
In the Scan Header field, add the value "user-agent"
In the Deny Strings field, add the values of the user-agents that must be blocked, one per line. In the example, is blocking the user-agents "hello" and "world"
You should add closer to this:

- Press OK and make a non-redirect following query with a specified user agent. Now it will return 404:
- Add the following configuration (where hello, world and helloworld are case-insensitive:
Code Select
# curl -Ik 10.69.45.153:8880 -A hello
HTTP/1.1 404 Not Found
Content-Length: 929
Content-Type: text/html
Server: Microsoft-IIS/10.0
X-Powered-By: ASP.NET
X-Content-Type-Options: nosniff
Date: Tue, 25 Mar 2025 14:47:08 GMT
Connection: closeUsing URL Rewriting Rules
To create a persistent rule in IIS on URL Rewriting, use the following steps:
1.Open IIS Manager (inetmgr).
2.Select the Server Node (not a specific site).
3.Open URL Rewrite.
4.Click "Add Rules..." on the right.
5.Choose Blank Rule under "Inbound Rules".
6.Click Edit... under "Conditions".
7.Click Add and configure:
- Name: Define a name for the rule, like "Block user-agent"
- Pattern: use ".*" to get all request (without the quotes)
- Condition Input: {HTTP_USER_AGENT}
- Check if the input string: "Matches the Pattern"
- Pattern: ".*(badbot|malicious-agent|exploit-scanner|hello|world).*" (Replace with actual user-agents and without the quotes)
8.Click OK.
9.In Action, select "Abort Request".
10.Click Apply and make a non-redirect following query with a specified user agent. Now it will return error aborting the connection:
Code Select
[code]# curl -Ik 10.69.45.153:8880 -A world
curl: (56) Recv failure: Connection reset by peer[/code]This solution is persistent across Plesk updates. It affects all IIS-hosted sites, including the Plesk Panel. It does not rely on web.config, which Plesk modifies.
Alternatively, if you prefer to edit the file manually, you can add the following content to file C:\Windows\System32\inetsrv\config\applicationHost.config inside <system.webServer> after line that starts with <proxy enabled="true"...:
CONFIGTEXT: <rewrite>
<rules>
<rule name="Block Bad User-Agents" stopProcessing="true">
<match url=".*" />
<conditions>
<add input="{HTTP_USER_AGENT}" pattern=".*(badbot|malicious-agent|exploit-scanner|hello|world).*" />
</conditions>
<action type="AbortRequest" />
</rule>
</rules>
</rewrite>
It will provide the same effect as the solution proposed above.
#87
Webserver / 502 Bad Gateway error on Plesk...
Last post by Suhitha - Sep 26, 2025, 03:15 AMQuestion: 502 Bad Gateway error on Plesk when using Comodo ModSecurity ruleset
Symptoms
AH00526: Syntax error on line 6035 of /etc/httpd/conf/modsecurity.d/rules/comodo_free/30_Apps_OtherApps.conf: Error creating rule: Error compiling pattern (offset 4): invalid range in character class
Cause
The mod_security package installed from the Atomic repository is not fully compatible with the current Comodo rule set.
Resolution
1.Connect to the Plesk server via SSH.
2.Execute the command to replace the ModSecurity package with the version provided by Plesk:
Symptoms
- All websites show a 502 Bad Gateway error
- Switching to the Atomic Standard ruleset resolves the problem
- The Plesk UI shows the following error message:
AH00526: Syntax error on line 6035 of /etc/httpd/conf/modsecurity.d/rules/comodo_free/30_Apps_OtherApps.conf: Error creating rule: Error compiling pattern (offset 4): invalid range in character class
Cause
The mod_security package installed from the Atomic repository is not fully compatible with the current Comodo rule set.
Resolution
1.Connect to the Plesk server via SSH.
2.Execute the command to replace the ModSecurity package with the version provided by Plesk:
Code Select
# dnf swap mod_security mod_security --enablerepo=PLESK_18_0_70-extras --disablerepo=atomic --skip-broken #88
Webserver / Websites hosted in Plesk are n...
Last post by Suhitha - Sep 26, 2025, 03:07 AMQuestion: Websites hosted in Plesk are not accessible after a recent Apache update: 421 Misdirected Request
Applicable to:
Symptoms
Cause
In recent Apache version, Apache team has released fixes for CVEs that affected Apache + nginx functionality: new changes do not allow Apache process requests from nginx without the server name (by default, nginx does not pass the server name through SNI when establishing a connection with a proxied HTTPS server).
Resolution
Install Plesk versions 18.0.70.3 or 18.0.71.1 to automatically resolve the issue.
Note: the hotfixes are compatible with the manual workaround. So, even for servers where manual solution is already applied, no extra steps are required after installing Plesk update.
As a manual workaround for previous Plesk versions:
Add proxy_ssl_server_name, proxy_ssl_name and proxy_ssl_session_reuse directives in nginx configuration to make nginx pass the server name to Apache through TLS Server Name Indication (SNI) extension:
1.Connect to the server via SSH
2.Run the script (without any modifications):
Applicable to:
- Plesk for Linux
Symptoms
- All websites show error:
Code Select
421 Misdirected RequestCode Select
The following error message is logged in domain's log ([b]Plesk > Domains > example.com > Logs[/b]):Code Select
AH02032: Hostname default-203_0_113_2 (default host as no SNI was provided) and hostname www.example.com provided via HTTP have no compatible SSL setupCause
In recent Apache version, Apache team has released fixes for CVEs that affected Apache + nginx functionality: new changes do not allow Apache process requests from nginx without the server name (by default, nginx does not pass the server name through SNI when establishing a connection with a proxied HTTPS server).
Resolution
Install Plesk versions 18.0.70.3 or 18.0.71.1 to automatically resolve the issue.
Note: the hotfixes are compatible with the manual workaround. So, even for servers where manual solution is already applied, no extra steps are required after installing Plesk update.
As a manual workaround for previous Plesk versions:
Add proxy_ssl_server_name, proxy_ssl_name and proxy_ssl_session_reuse directives in nginx configuration to make nginx pass the server name to Apache through TLS Server Name Indication (SNI) extension:
1.Connect to the server via SSH
2.Run the script (without any modifications):
Code Select
# echo -e "proxy_ssl_server_name on;\nproxy_ssl_name \$host;\nproxy_ssl_session_reuse off;" > /etc/nginx/conf.d/fixssl.conf && systemctl restart nginx #89
Webserver / Websites hosted in Plesk are i...
Last post by Suhitha - Sep 26, 2025, 02:59 AMQuestion: Websites hosted in Plesk are inaccessible and show HTTP 503 error
Symptoms
Cause
An issue with the imunify360 Proactive Defence module.
Resolution
The issue has been resolved by the CloudLinux team, and no further action is required. The affected components will be updated automatically to include the fix. More information about the incident can be found on the imunify360 status page.
Symptoms
- Websites hosted in Plesk are inaccessible and show an HTTP 503 or HTTP 504 error.
- Entries like the following can be found in /var/log/messages:
Code Select
Aug 19 12:15:14 [HOSTNAME] kernel: traps: php-fpm[PID] general protection fault ip:7f2e3875ecbf sp:7ffdbfc1c3c0 error:0 in libhs_runtime.so.5.4.0[7f2e3849c000+3b0000]
Aug 19 12:15:16 [HOSTNAME] kernel: traps: php-fpm[PID] general protection fault ip:7f2e3875ecbf sp:7ffdbfc1c3c0 error:0 in libhs_runtime.so.5.4.0[7f2e3849c000+3b0000]Cause
An issue with the imunify360 Proactive Defence module.
Resolution
The issue has been resolved by the CloudLinux team, and no further action is required. The affected components will be updated automatically to include the fix. More information about the incident can be found on the imunify360 status page.
#90
Webserver / Website is showing ERR_TOO_MAN...
Last post by Suhitha - Sep 26, 2025, 02:53 AMQuestion: Website is showing ERR_TOO_MANY_REDIRECTS, 404 or Default Plesk Page after updating Plesk to 18.0.72 version
Applicable to:
Symptoms
displaying Default Plesk Page or displaying 404 error.
Cause
The issue is caused by a Plesk bug with ID #PPPM-15085 already fixed in Plesk release 18.0.72.1 released on August 26th.
Resolution
If the fix does not work, there is a workaround to the issue: set the Default Site value to none in Plesk > Tools & Settings > IP Addresses:
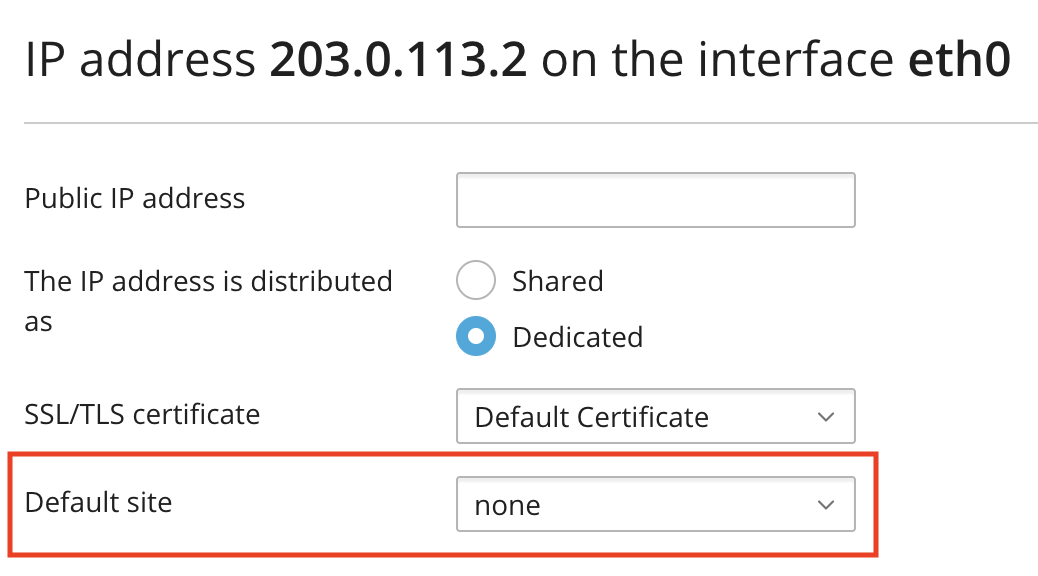
Applicable to:
- Plesk for Linux
Symptoms
- Plesk got recently updated to 18.0.72.
- Website is showing error
Code Select
ERR_TOO_MANY_REDIRECTS displaying Default Plesk Page or displaying 404 error.
- The affected website is configured as Default Site in Tools & Settings > IP Addresses.
Cause
The issue is caused by a Plesk bug with ID #PPPM-15085 already fixed in Plesk release 18.0.72.1 released on August 26th.
Resolution
If the fix does not work, there is a workaround to the issue: set the Default Site value to none in Plesk > Tools & Settings > IP Addresses:

